JupiterOne Platform
View assets, context, and risks in one place
Get complete visibility of all your cloud and on-premises assets. Visualize asset connections to see vulnerabilities and their blast radius. Get alerts when important changes occur. Automate compliance and audit evidence collection.

Collect and normalize assets
Map asset relationships
Query assets with natural language

Report insights instantly

Automate workflows

How it works

1. Collect and normalize asset data
Connect with all your security and infrastructure tools. 200+ integrations bring visibility into your cloud and on-premises assets.
2. Map out assets and relationships
Automatically reveal unmonitored assets and map relationships to uncover gaps and risks.

3. Total Visibility
Understand your entire attack surface to swiftly identify, prioritize, and remediate critical issues and vulnerabilities.
Features

Collect and normalize assets
API driven, agent-less collection of all assets across your tech stack. Consolidate asset data from IT, DevOps, security, HR, and other tools into a single source of truth.
Plus, see data from vulnerability scanners, security controls (like cryptographic keys), and other valuable context into the security state of assets.
View all modern cyber asset classes:
Map asset relationships
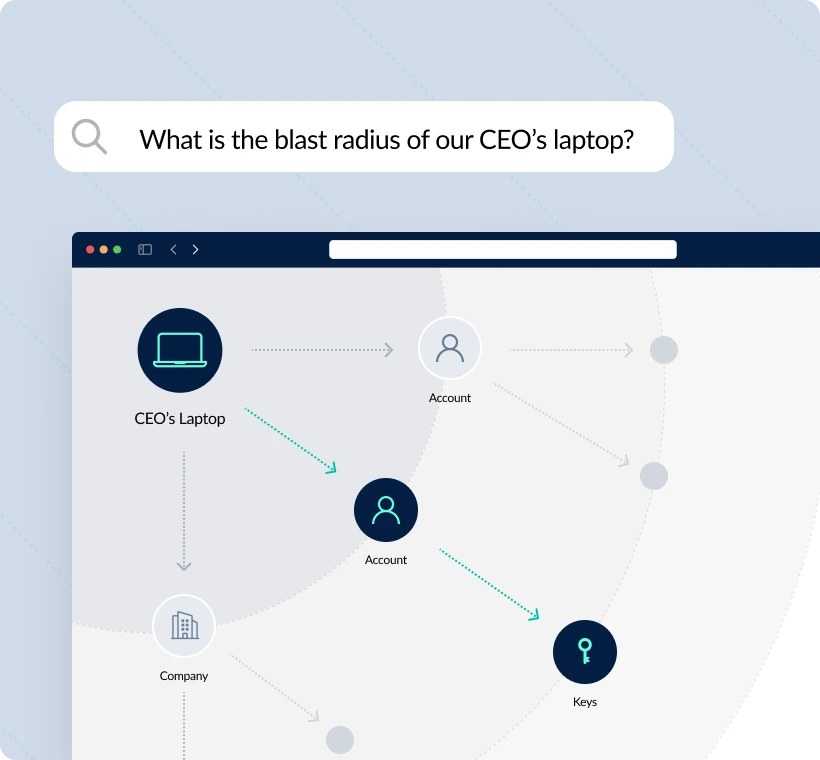
Visualize all the connections between your assets and uncover toxic combinations and hidden relationships that increase the risk of a material security incident.
See the blast radius of all the assets affected by security incidents. Detect downstream vulnerabilities.
Visualize connections between:


Query assets with natural language
Get detailed answers to any questions about your environment. Select queries from a pre-built library or create your own.
Quickly analyze your assets. Identify security gaps.
Search for:
Report insights instantly
Automate compliance and evidence collection for audits.
Continuously monitor for gaps. Quickly see non-compliant devices and hosts. See which users still need to complete security training. Update teams about issues.
Compliance frameworks:


Automate workflows
Pre-built dashboards view important asset data at a glance. Customize with widgets based on your most frequently used queries. Proactively notify teams with built-in and custom alerts.
Know where to start investigations and reduce incident response times.
Analyze asset details:
Over 200 integrations
Get visibility into your entire enterprise infrastructure
Award winning asset visibility & attack surface management software



Frequently Asked Questions
What is an asset?
Cyber assets are the on-prem and cloud resources included in a company's security and IT infrastructure. For example: apps, data, code repos, devices, networks, policies, security controls, users, configurations, and more.
A complete view of your assets in one platform helps you secure your entire cloud and hybrid environment.
What are common use cases for JupiterOne?
The most popular use cases include:
- Asset Management: Get complete visibility of all your assets and their connections.
- Vulnerability Prioritization: Map and triage vulnerabilities based on criticality.
- Incident Response: Instantly see the blast radius of affected assets following a breach.
- Compliance: Maintain industry standards and automate audit processes.
What tools does JupiterOne integrate with?
JupiterOne integrates with over 200 security, IT, DevOps, and HR tools. Pull infrastructure data from top tools including AWS, Azure, Google, Microsoft, Snowflake, Salesforce, Jira, Qualys, Okta, GitHub, and more.
See all integrations

How do I use queries to monitor my environment?
JupiterOne makes it easy to create custom reports that address particular security or compliance concerns. For example, you can generate queries about current vulnerabilities, access privileges, recent changes, unused hosts, devices, and more. Select from pre-built queries or create your own using natural language searches.
Turn commonly used queries into triggers that automatically alert teams of critical changes. Add queries to dashboards so you can monitor environment security at a glance. Reduce time spent manually monitoring your environment.
Prioritize with confidence with complete asset management and analysis
Get a Demo


































