Solutions
One Platform to Manage All Asset Security Across Your Organization
Get better visibility of all your assets. Drill down into asset details, connections, and vulnerabilities. See the impact of potential threats. Remediate security and compliance gaps.
Get a Demo



Why JupiterOne for CAASM
Teams Need a Complete Asset Inventory to Secure Their Entire Attack Surface
Many security teams are responsible for 165,000+ cyber assets. However, they’re often stored across disparate, disconnected platforms. This makes it difficult to analyze asset risk levels and prioritize vulnerabilities.
JupiterOne centralizes asset visibility into one place. Devices, users, networks, code repos, and more. Query assets using simple, natural language searches. Identify security gaps. Prioritize remediation based on risk of breach and severity.

Why JupiterOne for CSPM
Teams Can’t Protect Their Org Without Managing Their Cloud Security
Although CSPM tools provide great information into cloud environments, they only cover one piece of an attack surface. As a result, security teams can’t see how cloud incidents connect to the rest of their assets.
JupiterOne provides unified visibility into all the assets across your multi-cloud, on-prem, and SaaS environments. Identify risks and compliance drift. Instantly see how they affect critical assets. Auto-send remediation tickets to teams.

Why JupiterOne for Incident Response
Orgs Can’t Remediate Incidents Without an Understanding of Asset Relationships
Many organizations have their asset inventory and risk management across multiple systems and often can’t see how they connect. This makes it hard to catch incidents, diagnose causes, prioritize risk, and pinpoint remediation steps.
JupiterOne streamlines incident response by continuously monitoring all assets for suspicious code, unmanaged devices, misconfigured data, and risky behavior. View incidents’ blast radius and potential impact. Prioritize & remediate faster.

Why JupiterOne for Vulnerability Management
Teams Need to be Able to Prioritize and Remediate Vulnerabilities Across All Assets
Teams often use multiple security tools to manage vulnerabilities and only track CVEs and zero days. This leaves teams unable to get a complete picture of their attack surface, see how vulnerabilities and assets relate, and prioritize threats.
JupiterOne streamlines vulnerability management into one platform. Identify vulnerabilities, view their connections to your assets, and the potential impact to your attack surface. Auto-send recommended remediation steps to teams.
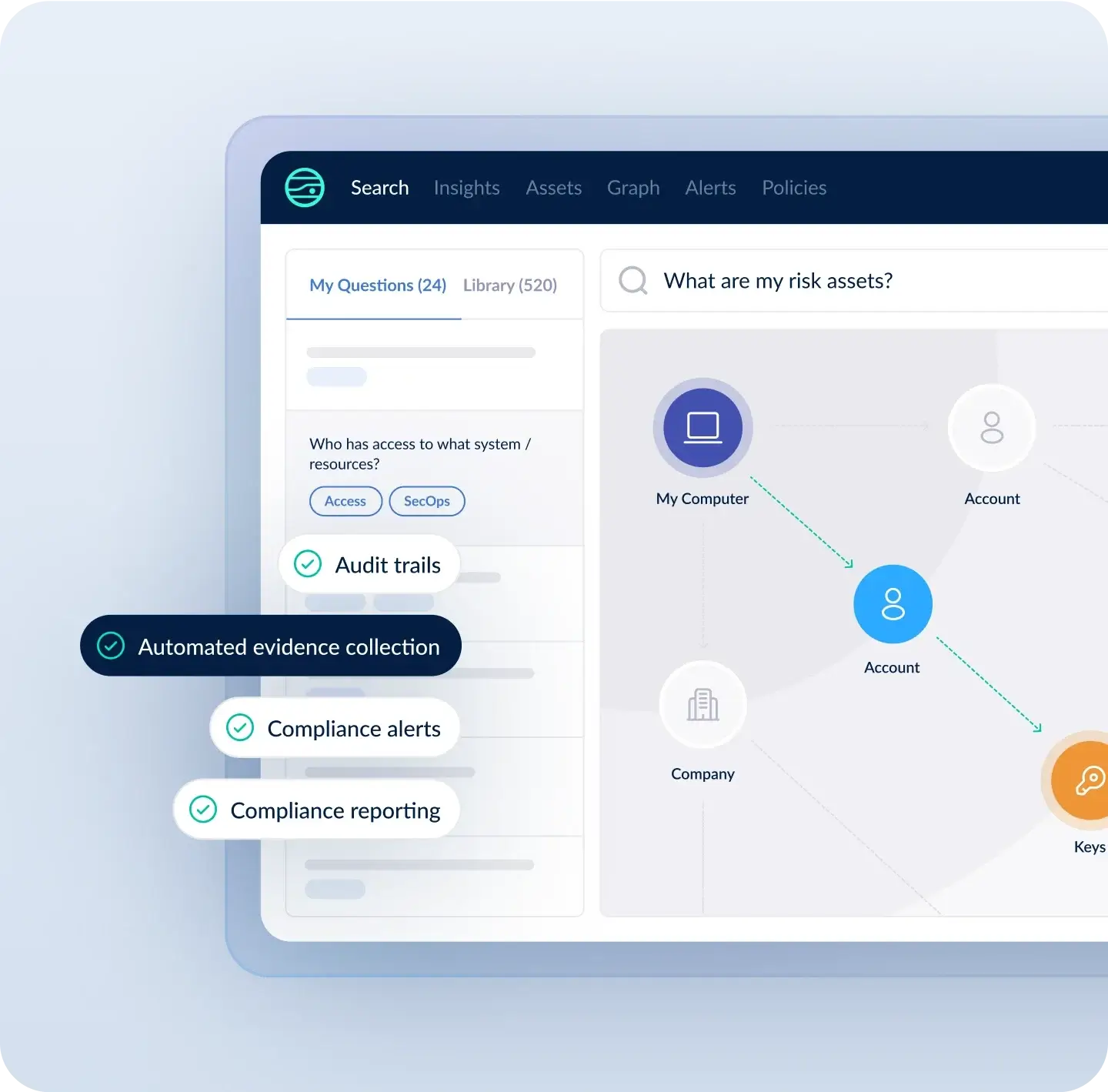
Why JupiterOne for IAM
Orgs Can’t Secure Their Environment Without Centralized User Identity Data
Teams often don’t have a centralized inventory of their user identities and permissions. This limits the ability to pinpoint user- and access-driven vulnerabilities, see which assets are at risk, and secure your attack surface.
JupiterOne centralizes user identity data to automate access reviews and spot misconfigurations. Auto-analyze access levels. Identify access risks connected to the most critical assets. Monitor permissions against security frameworks.

Why JupiterOne for Continuous Controls
Teams Can’t Stay Compliant Without Control Over Monitoring
Organizations struggle to stay up-to-date on control and compliance requirements for a number of reasons, including manual compliance checks, human oversight in security reviews, a lack of real-time monitoring and automated processes.
JupiterOne allows teams to continuously monitors controls and compliance. Monitor environment permissions against security standards, including NIST, ISO, CIS, SOC 2, and PCI-DSS. Or create custom frameworks. Streamline audits.
How It Works

All from a single platform
Unified Visibility
Finally get centralized visibility across all assets and their context. Devices, users, repos, networks, apps, and data.

Reduce attack surface
Unified Security Workflows
Quickly analyze your assets. See the blast radius of security incidents. Identify security gaps and compliance gaps.

Remediate faster
Identify & Remediate
Triage threats in minutes by risk of breach and severity. Auto-send tickets to Jira or other ticketing platform to teams.


































