I rode my bicycle across the United States in 1996 (Everett, Washington to Washington DC), and up into Nova Scotia. That summer I logged over 4400 miles on my bike. When I returned home to San Francisco in August, I had two passions: flying stunt kites, and learning about this new thing called "the internet". Both passions have stayed with me for over 25 years.
As a young kid, I used to build my own kites. There's a certain pride and power when something you've built from scratch gently pulls out of your hand, tethered to 200 feet of string, and then flies overhead for hours. Fast forward a couple decades, and I bought another Prism Stunt Kite last week. Let's just say I have more than one Prism at this point.
One of the first things you learn when flying a stunt kite is the concept of the "wind window". You can literally feel the window as you reach its edges and squirrelly things start to happen. I was reminded of that today when I heard of another security breach, with the release of a couple million records of private info. Let's examine a wind window for a sport kite, and then see how those concepts relate to security tools.
The Wind Window

Image: Working the Wind Window, from KiteLife.com
When flying a kite, the center of the wind window is called "the power zone". This is where the wind is most constant and most powerful. A beginner has a tendency to stay within the power zone because it's easy to feel the pull of the kite and maintain control. As you move outside the power zone, either up, left, or right, the pull of the kite becomes less and control is more by feel and experience. There is the possibility of stalling and losing control at the very edges of the window. Experienced flyers know where the window ends just by the feel of the strings against their fingers, actually using that change in pressure to execute more control, rather than less.
The Power Zone in the Security Window
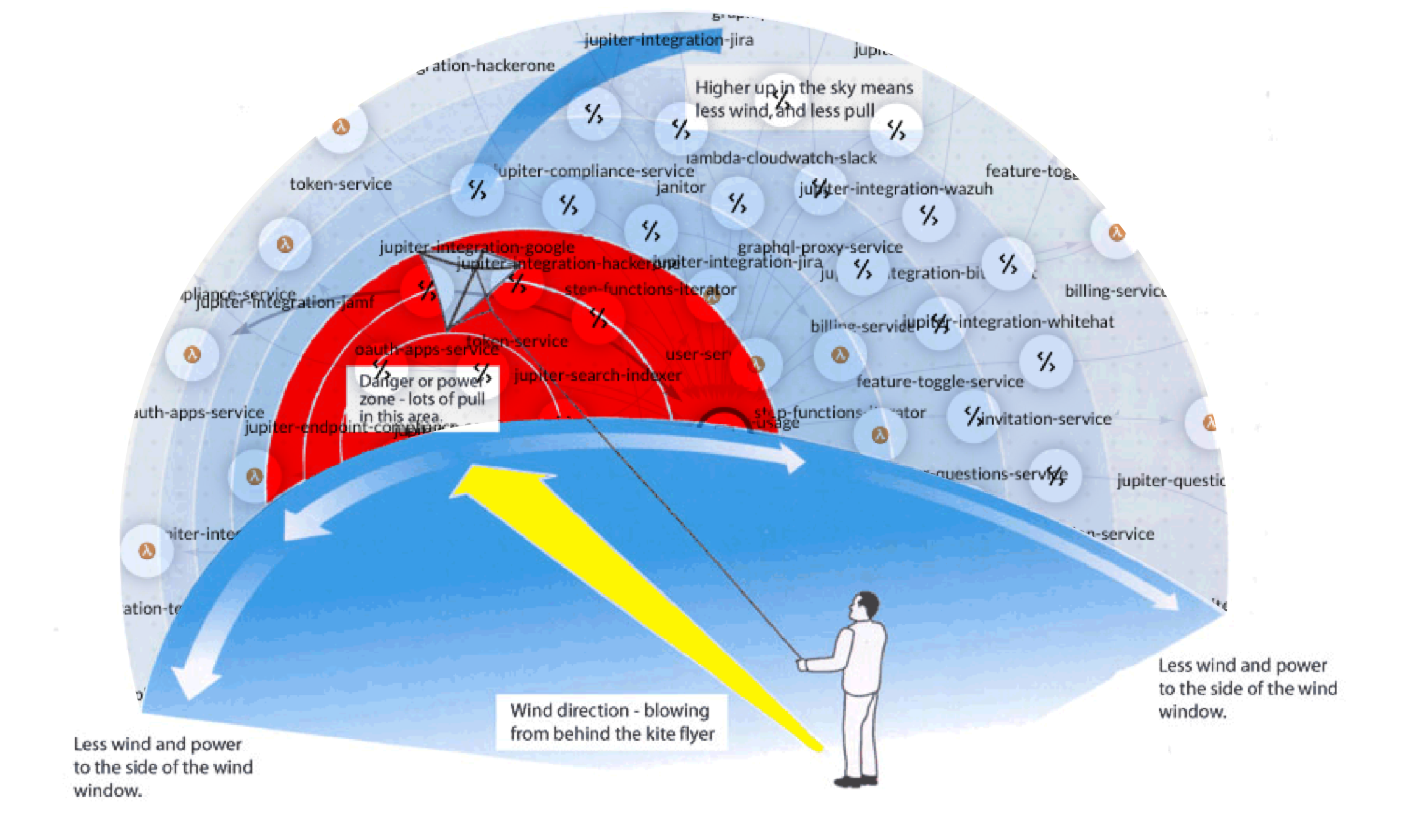
The Cyber Security Visibility Window
If we think of the various security tools on the market, most concentrate their focus in the "power zone", that area that is most susceptible to being exploited. You probably have a set of those tools, protecting against the most common forms of exploitation. Exploits occurring on the edge of the window have less visibility, if any at all, because they are not part of the "experience" of the tool set. What is lacking is visibility of the entire window, from the power zone through the edges of the window.
What is needed is a tool that serves two functions. First, it should aggregate the view of all of your current security tools into a single view, a centralized dashboard, which has visibility into all of your cyber assets. Second, the input from the various tools should be understood and displayed as part of interconnected relationships. This will allow visibility of output from tools monitoring the power zone, showing the relationship connections through to the edge of the security window. This relationship mapping exposes possible exploits that would not normally have triggered an alert from within the power zone.
That is what a cyber asset relationship map can provide. The power window shown in the graph above starts at the center of the graph, and expands through assets that are directly touching it, but is also capable of following the path to the end points of the diagram. This concept allows the visibility of relationships and how different assets affect each other.
How to Achieve Full Visibility of the Security Window

Security Window: Cyber Assets and their Connecting Relationships
The JupiterOne platform gives you visibility into your entire security window, from the power zone to the edges, by exposing your cyber assets into a consolidated dashboard, using your existing security tools as the data source. We have made the platform available for free, no cc required, no expiration date. You're welcome to take it out for a quick flight and discover where the edges of your security window are.
Happy flying!
Resources










